捕獲時間
2009-2-10
病毒摘要
該樣本是使用“ VC ”編寫的蠕蟲程序,由微點主動防御軟件自動捕獲,采用“PEtite”加殼方式試圖躲避特征碼掃描,加殼后長度為 “29,396字節”,圖標為“ ”,使用“exe”擴展名,通過“網頁木馬”、“文件捆綁”、“移動存儲介質”等途徑植入用戶計算機,運行后下載其他木馬到本地運行。
”,使用“exe”擴展名,通過“網頁木馬”、“文件捆綁”、“移動存儲介質”等途徑植入用戶計算機,運行后下載其他木馬到本地運行。
感染對象
Windows 2000/Windows XP/Windows 2003
傳播途徑
文件捆綁、網頁木馬、可移動存儲介質
防范措施
已安裝使用微點主動防御軟件的用戶,無須任何設置,微點主動防御將自動保護您的系統免受該病毒的入侵和破壞。無論您是否已經升級到最新版本,微點主動防御都能夠有效清除該病毒。如果您沒有將微點主動防御軟件升級到最新版,微點主動防御軟件在發現該病毒后將報警提示您發現“未知木馬”,請直接選擇刪除處理(如圖1);
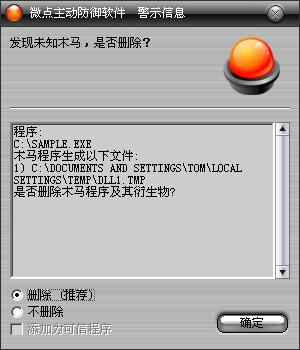
圖1 微點主動防御軟件自動捕獲未知病毒(未升級)
如果您已經將微點主動防御軟件升級到最新版本,微點將報警提示您發現"Worm.Win32.AutoRun.klb”,請直接選擇刪除(如圖2)。
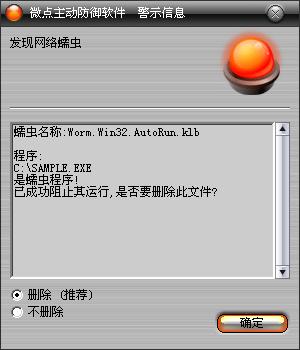
圖2 微點主動防御軟件升級后截獲已知病毒
對于未使用微點主動防御軟件的用戶,微點反病毒專家建議:
1、不要在不明站點下載非官方版本的軟件進行安裝,避免病毒通過捆綁的方式進入您的系統。
2、建議關閉U盤自動播放,具體操作步驟:開始->運行->gpedit.msc->計算機配置->管理模板->系統->在右側找到"關閉自動播放"->雙擊->選擇"已啟用"。
3、盡快將您的殺毒軟件特征庫升級到最新版本進行查殺,并開啟防火墻攔截網絡異常訪問,如依然有異常情況請注意及時與專業的安全軟件廠商聯系獲取技術支持。
4、開啟windows自動更新,及時打好漏洞補丁。
病毒分析
(1)、刪除指定的金山組件并釋放指定的病毒衍生物
(2)、嘗試結束指定的安全進程并停止指定服務
(3)、查找指定的360注冊表項,找到后進行特定的修改實現對360監控的關閉
(4)、關閉指定關鍵字的窗口
(5)、對大部分安全軟件進行映像劫持
(6)、修改文件的隱藏顯示
(7)、訪問指定網絡連接下載其他木馬到本地運行
(8)、對各個磁盤進行創建特定的AUTO文件,實現自動傳播
病毒刪除文件:
D:\Program Files\Kingsoft\Kingsoft Internet Security 2008
\kasbrowsershield.dll
%System32%\mfc71.dll
病毒創建文件:
%ProgramFiles%\ ALS.pif
%System32%\dllcache\linkinfo.dll
%Temp%\dll[隨機數字].tmp
%System32%\mfc1.dll
c:\AUTORUN.INF
c:\ZNZ.PIF
病毒結束進程
avp.exe
360Safe.exe
360tray.exe
360rpt.EXE
Runiep.exe
Rsaupd.exe
RAv.exe
RSTray.exe
CCenter.exe
RAVMON.exe
Ravservice.EXE
ScanFrm.exe
rsnetsvr.exe
RavTRAY.exe
RavMonD.exe
RsAgent.exe
GuardField.exe
Ravxp.exe
GFUpd.exe
kmailmon.exe
kavstart.exe
KAVPFW.EXE
kwatch.exe
kav32.exe
kissvc.exe
病毒停止服務:
Sharedaccess
McShield
KWhatchsvc
KPfwSvc
Kingsoft Internet Security Common Service
Symantec AntiVirus
norton AntiVirus server
DefWatch
Symantec AntiVirus Drivers Services
Symantec AntiVirus Definition Watcher
Norton AntiVirus Server
病毒刪除服務:
RavCCenter
RsScanSrv
RavTask
RsRavMon
病毒關閉窗口:
監視
監控
后門
NOD32
Process
瑞星
木馬
殺馬
綠鷹
Mcafee
Firewall
Virus
Anti
Worm
SREng
清理
下載者
病毒刪除注冊表:
項:
| |
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKLM\CurrentControlSet\Control\SafeBoot\Minimal{4D36E967-E325-11CE-BFC1-08002BE10318}
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318} |
|
項:
| |
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
鍵值:360Safetray
鍵值:360Safebox
鍵值:KavStart
鍵值:vptray
鍵值:ccApp
鍵值:RavTray |
|
病毒修改注冊表:
項:
| |
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\explorer\advanced\folder\hidden\showall
鍵值:CheckedValue
數據:2 |
|
項:
| |
HKLM\Software\360Safe\safemon
鍵值:ExecAccess
數據:0
鍵值:MonAccess
數據:0
鍵值:LeakShowed
數據:0
鍵值:SiteAccess
數據:0
鍵值:UDiskAccess
數據:0
鍵值:weeken
數據:0
鍵值:ARPAccess
數據:0
鍵值:IEProtAccess
數據:0
|
|
病毒創建注冊表:
項:
| |
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360rpt.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safe.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safebox.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360tray.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ANTIARP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ArSwp.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ast.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AutoRun.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AutoRunKiller.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AvMonitor.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVP.COM
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CCenter.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Frameworkservice.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GFUpd.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GuardField.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\HijackThis.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IceSword.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Iparmor.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KASARP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kav32.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVPFW.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kavstart.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kissvc.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kmailmon.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KPfwSvc.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KRegEx.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVMonxp.KXP
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVSrvXP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVWSC.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kwatch.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Mmsk.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapsvc.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nod32krn.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Nod32kui.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PFW.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQDoctor.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAV.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMon.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMonD.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ravservice.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavStub.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavTask.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAVTRAY.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Regedit.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwmain.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwProxy.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwsrv.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rfwstub.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RsAgent.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rsaupd.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RsMain.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rsnetsvr.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RSTray.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Runiep.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\safeboxTray.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ScanFrm.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SREngLdr.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojanDetector.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Trojanwall.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojDie.KXP
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPC32.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPTRAY.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WOPTILITIES.EXE
鍵值:debugger
數據:%System32%\dllcache\spoolsv.exe |
|
病毒訪問網絡:
| |
http://m. w**8.com/tt.txt
http://m. w**8.com/dd/x.gif
http://m. w**8.com/dd/1.exe
http://m. w**8.com/dd/2.exe
http://m. w**8.com/dd/6.exe
http://m. w**8.com/dd/9.exe
http://m. w**8.com/dd/10.exe |
|
