蠕蟲病毒
Worm.Win32.AutoRun.rzp
捕獲時間
2009-12-16
危害等級
中
病毒癥狀
該樣本是使用“Microsoft Visual C/C ”編寫的“蠕蟲病毒”,由微點(diǎn)主動防御軟件自動捕獲,采用“Upack”加殼方式試圖躲避特征碼掃描,加殼后長度為28,160字節(jié),圖標(biāo)為“ ”, 使用“ exe”擴(kuò)展名,通過網(wǎng)頁木馬、下載器下載、移動介質(zhì)(如U盤)等方式進(jìn)行傳播。
”, 使用“ exe”擴(kuò)展名,通過網(wǎng)頁木馬、下載器下載、移動介質(zhì)(如U盤)等方式進(jìn)行傳播。
用戶中毒后,會出現(xiàn)計算機(jī)及網(wǎng)絡(luò)運(yùn)行緩慢,安全軟件退出等現(xiàn)象。
感染對象
Windows 2000/Windows XP/Windows 2003/Windows Vista
傳播途徑
網(wǎng)頁掛馬、文件捆綁、下載器下載
防范措施
已安裝使用微點(diǎn)主動防御軟件的用戶,無須任何設(shè)置,微點(diǎn)主動防御將自動保護(hù)您的系統(tǒng)免受該病毒的入侵和破壞。無論您是否已經(jīng)升級到最新版本,微點(diǎn)主動防御都能夠有效清除該病毒。如果您沒有將微點(diǎn)主動防御軟件升級到最新版,微點(diǎn)主動防御軟件在發(fā)現(xiàn)該病毒后將報警提示您發(fā)現(xiàn)“未知木馬”,請直接選擇刪除處理(如圖1);
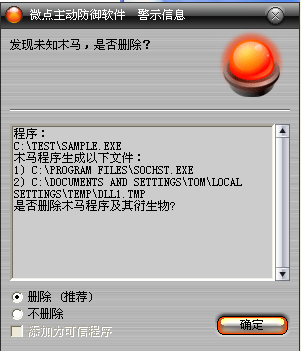
圖1 微點(diǎn)主動防御軟件自動捕獲未知病毒(未升級)
如果您已經(jīng)將微點(diǎn)主動防御軟件升級到最新版本,微點(diǎn)將報警提示您發(fā)現(xiàn)"Worm.Win32.AutoRun.rzp”,請直接選擇刪除(如圖2)。
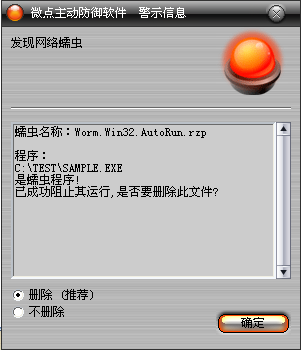
圖2 微點(diǎn)主動防御軟件升級后截獲已知病毒
未安裝微點(diǎn)主動防御軟件的手動解決辦法:
1、手動刪除以下文件:
%SystemDriver%\Fonts\tbh.ini
%temp%\dll2.tmp
X:\ HAZ.PIF
X:\ AutoRun.inf
X移動介質(zhì)。
2、手動刪除以下注冊表鍵:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\[安全軟件]
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ haot
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\aae
變量聲明:
%SystemDriver% 系統(tǒng)所在分區(qū),通常為“C:\”
%SystemRoot% WINDODWS所在目錄,通常為“C:\Windows”
%Documents and Settings% 用戶文檔目錄,通常為“C:\Documents and Settings”
%Temp% 臨時文件夾,通常為“C:\Documents and Settings\當(dāng)前用戶名稱\Local Settings\Temp”
%ProgramFiles% 系統(tǒng)程序默認(rèn)安裝目錄,通常為:“C:\ProgramFiles”
病毒分析
1、病毒運(yùn)行后遍歷進(jìn)程查找360rp.exe和360sd.exe,如果發(fā)現(xiàn)就刪除360rp服務(wù),結(jié)束360rp.exe和360sd.exe進(jìn)程。
2、檢查"%SystemRoot%\system32\arp.exe"是否存在,如果不存在就退出當(dāng)前進(jìn)程。
3、釋放并執(zhí)行病毒文件"%Program Files%\sochst.exe。
4、退出當(dāng)前進(jìn)程,調(diào)用命令行自我刪除。
5、在sochst.exe中,檢查"%SystemRoot%\system32\cmd.exe"是否存在,不存在就退出進(jìn)程。
6、查找病毒當(dāng)前目錄中是否存在AUTORUN.INF,如果存在,就執(zhí)行explorer.exe。
7、如果不存在就創(chuàng)建名稱為"LONGF"的互斥量,提升自己為"SeDebugPrivilege"權(quán)限。
8、創(chuàng)建線程,枚舉窗口,遍歷進(jìn)程,如果發(fā)現(xiàn)avp.exe、360sd.exe、rstray.exe、ravmond.exe等進(jìn)程,就關(guān)閉這些進(jìn)程創(chuàng)建的窗口;如果存在kswebshield.exe、kav32.exe、kpfw32.exe、vptray.exe、mctray.exer、tvscan.exe、vpc32.exe、mcshiled.exe進(jìn)程,就通過釋放其內(nèi)存使這些進(jìn)程退出;如果發(fā)現(xiàn)ekrn.exe,就刪除ekrn服務(wù),結(jié)束ekrn.exe和egui.exe進(jìn)程;如果發(fā)現(xiàn)nod32krn.exe,就刪除nod32krn服務(wù),結(jié)束nod32krn.exe和nod32kui.exe進(jìn)程。
9、釋放并加載動態(tài)庫文件"%SystemDriver%\yansl.dll",并設(shè)置為系統(tǒng)、隱藏屬性。
10、在yansl.dll中,釋放驅(qū)動文件"%SystemDriver%\WINDOWS\Fonts\pci.sys",創(chuàng)建名稱為"aae"的服務(wù),恢復(fù)SSDT,遍歷查找并結(jié)束
360safe.exe、360tray.exe、safeboxtray.exe、360safebox.exe、krnl360svc.exe、zhudongfangyu.exe、rstray.exe、360sd.exe、360rp.exe、kavstart.exe、kswebshield.exe、Mcshield.exe等進(jìn)程,刪除安全軟件相關(guān)文件,最后刪除驅(qū)動文件。
11、創(chuàng)建線程,釋放并加載動態(tài)庫文件dll2.tmp,在dll2.tmp中,創(chuàng)建大量安全軟件的映像劫持,查找兵刃窗口,如果找到就發(fā)送消息使其退出,連接網(wǎng)絡(luò),下載病毒列表,根據(jù)列表下載病毒到本地運(yùn)行。
12、創(chuàng)建線程,遍歷查找avp.exe,找到后通過卸載avp進(jìn)程模塊,使進(jìn)程退出,停止avp相關(guān)服務(wù)。
13、刪除動態(tài)庫文件yansl.dll。
14、檢查"%SystemDriver%\system32\dllcache\linkinfo.dll"是否存在,不存在就拷貝"%SystemDriver%\system32\linkinfo.dll"到此文件夾,釋放驅(qū)動文件"%SystemDriver%\Fonts\haot.sys",創(chuàng)建名稱為"haot"的服務(wù),感染"%SystemDriver%\system32\linkinfo.dll"。
15、遍歷磁盤,在每個磁盤下創(chuàng)建AUTORUN.INF和HAZ.PIF。
病毒創(chuàng)建文件:
%SystemDriver%\Fonts\haot.sys
%SystemDriver%\Fonts\tbh.ini
%SystemDriver%\Fonts\pci.sys
%SystemDriver%\yansl.dll
%temp%\dll2.tmp
X:\ HAZ.PIF
X:\ AutoRun.inf
X移動介質(zhì)。
病毒刪除文件:
%SystemDriver%\Fonts\haot.sys
%SystemDriver%\Fonts\pci.sys
%SystemDriver%\yansl.dll
病毒修改文件:
%SystemDriver%\system32\linkinfo.dll
病毒創(chuàng)建注冊表:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360rp.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360rpt.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safe.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safebox.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safeup.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360sd.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360tray.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360upp.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ANTIARP.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\arpfw.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ArSwp.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ast.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AutoRun.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AutoRunKiller.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AvMonitor.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avp.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CCenter.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ccEvtMgr.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Frameworkservice.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GFUpd.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GuardField.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\HijackThis.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IceSword.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Iparmor.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KASARP.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kav32.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVPFW.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kavstart.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kissvc.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KpfwSvc.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KRegEx.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\krnl360svc.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KSWebShield.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVMonxp.KXP]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVSrvXP.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVWSC.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kwatch.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LiveUpdate360.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mcshield.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Mmsk.EXE
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\naPrdMgr.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapsvc.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nod32krn.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Nod32kui.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PFW.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAV.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMon.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMonD.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ravservice.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavStub.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavTask.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAVTRAY.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwmain.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwProxy.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwsrv.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rfwstub.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RsAgent.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rsaupd.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RsMain.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RSTray.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Runiep.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\safeboxTray.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ScanFrm.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SREngLdr.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojanDetector.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Trojanwall.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojDie.KXP]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPC32.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPTRAY.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VsTskMgr.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WOPTILITIES.EXE]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ZhuDongFangYu.EXE]
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ haot
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\aae
