蠕蟲程序
Worm.Win32.AutoRun.vku
捕獲時間
2011-04-14
危害等級
中
病毒癥狀
該樣本是使用“VC ”編寫的“蠕蟲程序”,由微點主動防御軟件自動捕獲, 采用“UPX”加殼方式,企圖躲避特征碼掃描,加殼后長度為“83,210”字節,圖標為“ ”,使用“exe”擴展名,通過文件捆綁、網頁掛馬、下載器下載等方式進行傳播。病毒主要目的是盜取用戶信息,創建流氓廣告圖標,點擊后獲取網絡流量。 ”,使用“exe”擴展名,通過文件捆綁、網頁掛馬、下載器下載等方式進行傳播。病毒主要目的是盜取用戶信息,創建流氓廣告圖標,點擊后獲取網絡流量。
感染對象
Windows 2000/Windows XP/Windows 2003/Windows Vista/ Windows 7
傳播途徑
文件捆綁、網頁掛馬、下載器下載
防范措施
已安裝使用微點主動防御軟件的用戶,無須任何設置,微點主動防御將自動保護您的系統免受該病毒的入侵和破壞。無論您是否已經升級到最新版本,微點主動防御都能夠有效清除該病毒。如果您沒有將微點主動防御軟件升級到最新版,微點主動防御軟件在發現該病毒后將報警提示您發現“未知間諜”,請直接選擇刪除處理(如圖1)
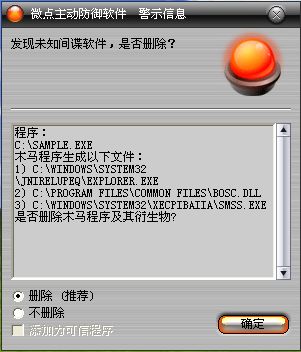
圖1 微點主動防御軟件自動捕獲未知病毒(未升級)
如果您已經將微點主動防御軟件升級到最新版本,微點將報警提示您發現木馬"Worm.Win32.AutoRun.vku”,請直接選擇刪除(如圖2)。
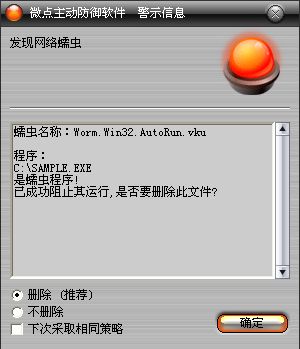
圖2 微點主動防御軟件升級后截獲已知病毒
未安裝微點主動防御軟件的手動解決辦法:
1.手動刪除文件
刪除 %SystemRoot%\system32\jnirelupeq\explorer.exe
刪除 %SystemRoot%\system32\xecpibaiia\smss.exe
刪除 %SystemDriver%\gwyivodjab.txt(隨機名)
刪除 %SystemDriver%\hccguiacas.jpg(隨機名)
刪除 %SystemDriver%\tvaaixmniw.gif(隨機名)
刪除 %SystemDriver%\fyisyelrhy.doc(隨機名)
刪除 %SystemDriver%\qrkgwteuwg.bmp(隨機名)
刪除 %SystemDriver%\Program Files\Common Files\BOSC.dll
刪除 %SystemDriver%\q9q.dll
刪除 %SystemRoot%\System32\drivers\kpscc.sys
刪除 X:\ My Documamts.exe(各個磁盤根目錄)
2.手動刪除注冊表
刪除 HKEY_LOCAL_MACHINE\system\CurrentControlSet\Services\Dmusic
名稱:ImagePath
數據:\??\C:\WINDOWS\System32\drivers\kpscc.sys
刪除 HKEY_LOCAL_MACHINE\SOFTWARE\Thunder Network\ThunderOem\thunder_backwnd
名稱:Path
數據:C:\q9q.dll
刪除 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\EXPLORER\run
名稱:xecpibaiia
數據:C:\WINDOWS\System32\xecpibaiia\smss.exe
刪除 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\EXPLORER\run
名稱:jnirelupeq
數據:C:\WINDOWS\System32\jnirelupeq\explorer.exe
刪除 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\下大量被劫持項
刪除 HKEY_CLASSES_ROOT\exefile
名稱:NeverShowExt
數據:1
刪除 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
名稱:ModRiskFileTypes
數據:.exe
查找與CLSID {F986CC17-37C0-4585-B7D9-15F2161F0584}相關的項刪除。
3.手動導入正確的注冊表
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\{4D36E969-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\Directory\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\RisingRavExt
HKEY_CLASSES_ROOT\Directory\shellex\ContextMenuHandlers\RisingRavExt
HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers\RisingRavExt
4.下載微點流氓桌面清除工具和微點文件夾病毒清除工具進行查殺。
變量聲明:
%SystemDriver% 系統所在分區,通常為“C:\”
%SystemRoot% WINDODWS所在目錄,通常為“C:\Windows”
%Documents and Settings% 用戶文檔目錄,通常為“C:\Documents and Settings”
%Temp% 臨時文件夾,通常為“C:\Documents and Settings\當前用戶名稱\Local Settings\Temp”
%ProgramFiles% 系統程序默認安裝目錄,通常為:“C:\ProgramFiles”
病毒分析:
1.建立進程快照查找avp.exe等殺軟進程,如果查找到,先判斷"C:\RECYCLER"文件夾和"C:\Recovery"文件夾以及"C:\System Volume Information"文件夾的屬性是否為系統只讀屬性,如果是,繼續執行后面的程序。
2.如果沒有查找到,遍歷用戶磁盤根目錄信息。然后建立線程函數,目的是將"cmd.exe","netsh.exe","conime.exe","regedit.exe","wscript.exe","regsvr32.exe","rundll32.exe","wmiprvse.exe","ipconfig.exe"等進程終止結束掉。
3. 如果有已命名互斥體對象"ca6f06b7575bf3a0b24462db96e36efe1"和"ca6f06b7575bf3a0b24462db96e36efe2"創建一個新句柄,主要是防止程序多次運行。如果沒有該已命名互斥體對象,就繼續往下執行。
4.創建文件夾目錄:“C:\WINDOWS\system32\xecpibaiia”和“C:\WINDOWS\system32\jnirelupeq”休眠1s時間,然后遍歷文件查找" C:\WINDOWS\system32\jnirelupeq\explorer.exe ",
如果找到,將該文件轉換成本地時間以及dos時間和日期,并設置" C:\WINDOWS\system32\jnirelupeq\explorer.exe "正常屬性,著刪除" C:\WINDOWS\system32\jnirelupeq\explorer.exe "文件。
如果沒有找到 ,遍歷文件查找" C:\WINDOWS\system32\xecpibaiia\smss.exe ",如果找到,將文件轉換成本地時間和dos時間,并設置" C:\WINDOWS\system32\xecpibaiia\smss.exe "正常屬性,刪除" C:\WINDOWS\system32\xecpibaiia\smss.exe "文件。
5.休眠一定時間,然后將病毒自身以替換的方式拷貝并重新命名為:“C:\WINDOWS\system32\xecpibaiia\smss.exe”和“C:\WINDOWS\system32\jnirelupeq\explorer.exe”,緊接著分別啟動這兩個相應的進程。
6.建立互斥體變量“ca6f06b7575bf3a0b24462db96e36efe1”防止程序多次運行。然后提升當前用戶進程權限為"SeDebugPrivilege",并建立線程函數,線程函數主要是休眠3s時間,遍歷文件查找"C:\Program Files\Internet Explorer\iexplore.exe",找到以后將該文件轉換成本地時間以及dos時間和日期,創建文件:“C:\gwyivodjab.txt”, “C:\hccguiacas.jpg”, “C:\tvaaixmniw.gif”, “C:\fyisyelrhy.doc”, “C:\qrkgwteuwg.bmp”并設置相應的正常文件屬性,這5個文件都是隨機的名稱。如果沒有找到,就在其他D:盤符建立5個隨機名稱的文件。創建文件夾:“C:\VSPS”并在將病毒自身以替換的方式拷貝并重新命名為:“C:\VSPS\VSPS.exe”并設置文件和文件夾的屬性為系統隱藏屬性。緊接著建立進程快照,查找進程名為:"RsTray.exe","360tray.exe",找到以后退出主程序。如沒有找到,先刪除"C:\Program Files\Common Files\BOSC.dll"文件,然后在同一樣的目錄下建立"C:\Program Files\Common Files\BOSC.dll"文件,并加載之。以"InstallHook"為參數建立全局的鍵盤和鼠標鉤子。以"HideProcess"參數隱藏相應的進程。并將該Dll文件設置為系統隱藏屬性。
7. 建立互斥體變量“ca6f06b7575bf3a0b24462db96e36efe2”防止程序多次運行。然后提升當前用戶進程權限為"SeDebugPrivilege",并建立線程函數,線程函數主要是將"cmd.exe","netsh.exe","conime.exe","regedit.exe","wscript.exe","regsvr32.exe","rundll32.exe","wmiprvse.exe","ipconfig.exe"等進程終止結束掉。然后將病毒自身設置為系統隱藏屬性,休眠3s時間,遍歷文件查找"C:\WINDOWS\System32\reg.exe","C:\WINDOWS\System32\wscript.exe","C:\WINDOWS\regedit.exe"等文件,如果找到,將該文件轉換成本地時間以及dos時間和日期,然后讀取這3個相應文件之后沒有釋放該文件的句柄,目的是使用戶不能使用這3個文件。如果沒有找到就退出程序。設置注冊表信息:HKEY_LOCAL_MACHINE\SOFTWARE\TENCENT\QQ2009,鍵值為:Install,遍歷文件查找" "C:\Program Files\Tencent\QQ\Bin\Shareds.dll",如果找到,將該文件轉換成本地時間以及dos時間和日期,如果沒有找到,將
"C:\q9q.dll"文件設置為系統隱藏屬性,然后刪除,休眠300ms時間,緊接著創建"C:\q9q.dll"文件,休眠300ms時間,遍歷文件查找" C:\q9q.dll "如果找到,將該文件轉換成本地時間以及dos時間和日期,然后將"C:\Program Files\Tencent\QQ\Bin\TaskTray.dll"以移動方式并重新命名到"C:\Program Files\Tencent\QQ\Bin\Shareds.dll",休眠300ms時間,緊接著將剛剛創建的"C:\q9q.dll"文件以移動的方式并重新命名到"C:\Program Files\Tencent\QQ\Bin\TaskTray.dll",休眠2s時間,遍歷文件查找" C:\q9q.dll "如果找到,將該文件轉換成本地時間以及dos時間和日期。如果沒有找到,設置注冊表信息:HKEY_LOCAL_MACHINE\SOFTWARE\TENCENT\QQ,鍵值為:Install,以及HKEY_LOCAL_MACHINE\SOFTWARE\Thunder Network\ThunderOem\thunder_backwnd 名稱:path ,數據:"C:\q9q.dll",將"C:\Program Files\"文件夾設置系統隱藏屬性。還有將“C:\Documents and Settings\All Users\「開始」菜單\程序\啟動\xinabini.exe”文件設置為系統隱藏屬性,以及“C:\Documents and Settings\當前用戶\「開始」菜單\程序\啟動\pbkxjkmeqm.exe”文件設置為系統隱藏屬性。
8.獲取“C:\WINDOWS\system32\drivers”目錄信息。遍歷查找"C:\WINDOWS\System32\drivers\kpscc.sys"文件,如果沒有,就建立驅動文件。并建立相應的服務注冊表信息:
HKEY_LOCAL_MACHINE\system\CurrentControlSet\Services\Dmusic
名稱:ImagePath
數據:\??\C:\WINDOWS\System32\drivers\kpscc.sys
9.然后建立管道"\\.\MYFL",與驅動進行通信,終止結束相關的殺軟進程。并在注冊表項HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options下建立大量新鍵值劫持大量安全軟件,使其不能運動。并分別再次以外部命令的方式啟動" C:\WINDOWS\system32\xecpibaiia\smss.exe " 進程和“C:\WINDOWS\system32\ jnirelupeq\explorer.exe”進程。
10.該病毒將"C:\WINDOWS\system32\drivers\etc\hosts"文件,"C:\recycler\winlogon.exe"文件,"C:\WINDOWS\System32\RavExt.dll"文件,"C:\WINDOWS\System32\bsmain.exe"文件通過移動的方式,重新啟動刪除這些文件。
刪除應用于360和瑞星殺軟的右鍵菜單項于注冊表的項:
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\Directory\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\RisingRavExt
HKEY_CLASSES_ROOT\Directory\shellex\ContextMenuHandlers\RisingRavExt
HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers\RisingRavExt
11.修改注冊表鍵值:目的是使隱藏文件和文件夾不可見.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
名稱:ShowSuperHidden
數據:0
修改注冊表鍵值:目的是使桌面IE圖標不可用。
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
名稱: {871C5380-42A0-1069-A2EA-08002B30309D}
數據:1
創建注冊表信息:目的是使用戶不可使用Windows經典桌面主題
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
名稱:{871C5380-42A0-1069-A2EA-08002B30309D}
數據:1
12.刪除" C:\Documents and Settings\當前用戶\桌面\360殺毒.lnk"快捷方式,刪除" C:\Documents and Settings\當前用戶\桌面\360保險箱.lnk"快捷方式,刪除" C:\Documents and Settings\當前用戶\桌面\360安全衛士.lnk"快捷方式,刪除" C:\Documents and Settings\當前用戶\桌面\360軟件管家.lnk"快捷方式,刪除" C:\Documents and Settings\當前用戶\桌面\QQ瀏覽器 5.lnk"快捷方式,
刪除" C:\Documents and Settings\All Users\「開始」菜單\QQ瀏覽器5.lnk"快捷方式"快捷方式,刪除" C:\Documents and Settings\All Users\「開始」菜單\360安全瀏覽器 3.lnk"快捷方式"快捷方式,刪除" C:\Documents and Settings\當前用戶\桌面\修復360安全衛士.url"快捷方式,刪除" C:\Documents and Settings\All Users\桌面\修復瑞星軟件.lnk"快捷方式,刪除" C:\Documents and Settings\All Users\桌面\瑞星殺毒軟件.lnk"快捷方式,刪除" C:\Documents and Settings\All Users\桌面\瑞星個人防火墻.lnk"快捷方式,刪除" C:\Documents and Settings\All Users\桌面\360安全瀏覽器 3.lnk"快捷方式,
13.設置"C:\Documents and Settings\All Users\「開始」菜單\程序\360殺毒"文件的系統隱藏屬性,設置"C:\Documents and Settings\當前用戶\「開始」菜單\程序\360保險箱"文件系統隱藏屬性,設置"C:\Documents and Settings\當前用戶\「開始」菜單\程序\360安全衛士"文件的系統隱藏屬性,設置"C:\Program Files\Kaspersky Lab"文件的系統隱藏屬性,設置" C:\Documents and Settings\All Users\「開始」菜單\程序\瑞星個人防火墻"文件的系統隱藏屬性,設置" C:\Documents and Settings\All Users\「開始」菜單\程序\瑞星個人防火墻"文件的系統隱藏屬性,設置" C:\Documents and Settings\All Users\「開始」菜單\程序\瑞星殺毒軟件"文件的系統隱藏屬性,設置"C:\Documents and Settings\當前用戶\「開始」菜單\程序\騰訊軟件\QQ瀏覽器 5"文件系統隱藏屬性,設置"C:\Documents and Settings\All Users\「開始」菜單\程序\360安全瀏覽器 3"文件系統隱藏屬性,設置"C:\Documents and Settings\當前用戶\「開始」菜單\程序\卡巴斯基反病毒軟件 7.0"文件系統隱藏屬性,設置"C:\Documents and Settings\當前用戶\「開始」菜單\程序\卡巴斯基反病毒軟件 2010"文件系統隱藏屬性,設置"C:\Documents and Settings\當前用戶\「開始」菜單\程序\卡巴斯基反病毒軟件 2009"文件系統隱藏屬性,設置"C:\Documents and Settings\ All Users \「開始」菜單\程序\卡巴斯基反病毒軟件 2010"文件系統隱藏屬性,設置"C:\Documents and Settings\ All Users \「開始」菜單\程序\卡巴斯基反病毒軟件 7.0"文件系統隱藏屬性,設置"C:\Documents and Settings\ All Users \「開始」菜單\程序\卡巴斯基反病毒軟件 2009"文件系統隱藏屬性,設置" C:\Documents and Settings\當前用戶\桌面\卡巴斯基反病毒軟件 2009.lnk"快捷方式的系統隱藏屬性,設置" C:\Documents and Settings\當前用戶\桌面\卡巴斯基反病毒軟件 2010.lnk"快捷方式的系統隱藏屬性,設置" C:\Documents and Settings\ All Users \桌面\卡巴斯基反病毒軟件 2009.lnk"快捷方式的系統隱藏屬性,設置" C:\Documents and Settings\ All Users \桌面\卡巴斯基反病毒軟件 2010.lnk"快捷方式的系統隱藏屬性。
14.建立注冊表信息:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}
名稱:InfoTip 數據:@shdoclc.dll,-881
名稱:LocalizedString 數據:@shdoclc.dll,-880
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\shell\OpenHomePage\Command
名稱:默認
數據:iexplore.exe http://www.sfc006.com/?Activex
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\shell\屬性(&R)\Command
名稱:默認
數據:rundll32.exe shell32.dll,Control_RunDLL inetcpl.cpl,,0
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\shell\OpenHomePage
名稱:默認 數據:打開主頁
名稱:MUIVerb 數據:@shdoclc.dll,-10241
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\Shellex\ContextMenuHandlers\ieframe
名稱:默認
數據:{871C5380-42A0-1069-A2EA-08002B30309D}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\ShellFolder
名稱:Attributes
數據:0
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\shell
名稱:OpenHomePage
數據:默認
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\InProcServer32
名稱:默認 數據:%SystemRoot%\system32\shdocvw.dll
名稱:ThreadingModel 數據:Apartment
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\DefaultIcon
名稱:默認
數據:shdoclc.dll,-190
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\InfoTip
名稱:默認
數據:@shdoclc.dll,-881
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F986CC17-37C0-4585-B7D9-15F2161F0584}\LocalizedString
名稱:默認
數據:@shdoclc.dll,-880
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace\{F986CC17-37C0-4585-B7D9-15F2161F0584}\InProcServer32
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
名稱:{871C5380-42A0-1069-A2EA-08002B30309D}
數據:1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
名稱:{871C5380-42A0-1069-A2EA-08002B30309D}.default
數據:0
15.遍歷文件,查找" C:\Documents and Settings\當前用戶\桌面\Internet Explorer.lnk","C:\Documents and Settings\當前用戶\桌面\改變你的一生.url"、" C:\Documents and Settings\當前用戶\桌面\淘寶購物A.url"," C:\Documents and Settings\All Users\桌面\免費電影C.url "等快捷方式,更改其創建時間,并設置為系統隱藏屬性。
16.遍歷各個磁盤根目錄,在各個目錄下將病毒自身以拷貝的方式創建“My Documamts.exe”文件。然后偽裝成文件夾的形式,誘導用戶點擊該病毒文件。
17.刪除注冊表項信息:目的是使用戶無法進入到安全模式:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\{4D36E969-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
病毒創建文件:
%SystemRoot%\system32\jnirelupeq\explorer.exe
%SystemRoot%\system32\xecpibaiia\smss.exe
%SystemDriver%\gwyivodjab.txt(隨機名)
%SystemDriver%\hccguiacas.jpg(隨機名)
%SystemDriver%\tvaaixmniw.gif(隨機名)
%SystemDriver%\fyisyelrhy.doc(隨機名)
%SystemDriver%\qrkgwteuwg.bmp(隨機名)
%SystemDriver%\Program Files\Common Files\BOSC.dll
%SystemDriver%\q9q.dll
%SystemRoot%\System32\drivers\kpscc.sys
X:\ My Documamts.exe(各個磁盤根目錄)
%ProgramFiles%\Tencent\QQ\Bin\Shareds.dll
%ProgramFiles%\Tencent\QQ\Bin\TaskTray.dll
%SystemRoot%\system32\drivers\etc\hosts
%SystemDriver%\recycler\winlogon.exe
%SystemRoot%\System32\RavExt.dll
%SystemRoot%\System32\bsmain.exe
病毒創建注冊表:
HKEY_LOCAL_MACHINE\SOFTWARE\Thunder Network\ThunderOem\thunder_backwnd
名稱:path
數據:"C:\q9q.dll
HKEY_LOCAL_MACHINE\system\CurrentControlSet\Services\Dmusic
名稱:ImagePath
數據:\??\C:\WINDOWS\System32\drivers\kpscc.sys
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\EXPLORER\run
名稱:xecpibaiia
數據:C:\WINDOWS\System32\xecpibaiia\smss.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\EXPLORER\run
名稱:jnirelupeq
數據:C:\WINDOWS\System32\jnirelupeq\explorer.exe
HKEY_CLASSES_ROOT\exefile
名稱:NeverShowExt
數據:1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
名稱:ModRiskFileTypes
數據:.exe
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\StorageDevicePolicies
名稱:WriteProtect
數據:0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
名稱:{871C5380-42A0-1069-A2EA-08002B30309D}
數據:1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\safeboxTray.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360Safe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safebox.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360tray..exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ravcopy.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AvastU3.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ScanU3.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AvU3Launcher.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQPCMgr.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\runiep.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwmain.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwsrv.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVPF.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KPFW32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nod32kui.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nod32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapsvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SelfUpdate.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQPCRTP.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapw32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avconsol.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\webscanx.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NPFMntor.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vsstat.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zjb.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KPfwSvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ QQDoctorMain.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RavTask.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ atpup.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ mmsk.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ WoptiClean.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ QQKav.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ EGHOST.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ QQDoctor.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RegClean.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ FYFireWall.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ iparmo.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ adam.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KWSMain.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ IceSword.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ 360rpt.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ AgentSvr.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ AppSvc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ autoruns.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ avgrssvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ DSMain.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ 360sd.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kwstray.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ knsd.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ AvMonitor.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ CCenter.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ ccSvcHst.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ FileDsty.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ FTCleanerShell.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ HijackThis.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ Iparmor.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ isPwdSvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KSWebShield.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kabaload.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KaScrScn.SCR
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KASMain.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KASTask.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ AntiU.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KAV32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KAVDX.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KAVPFW.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KAVSetup.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ ArSwp2.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KISLnchr.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KMailMon.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KMFilter.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KPFW32X.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KPFWSvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KRegEx.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KsLoader.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KVCenter.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ ArSwp3.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KvDetect.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KvfwMcl.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KVMonXP.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KVMonXP_1.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kvol.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kvolself.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KVScan.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KVSrvXP.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KVStub.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kvupload.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kvwsc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KvXP.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KvXP_1.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KWatch.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KWatch9x.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KWatchX.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ loaddll.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ MagicSet.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ PFW.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ mcconsol.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ QQPCTray.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ nod32krn.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ PFWLiveUpdate.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ QHSET.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RavStub.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ Ras.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ rfwcfg.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RfwMain.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RsAgent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ Rsaupd.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ safelive.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ knsdave.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ irsetup.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ scan32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ shcfg32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ SmartUp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ SREng.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ symlcsvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ SysSafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ TrojanDetector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ Trojanwall.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KWSUpd.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UIHost.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UmxAgent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UmxAttachment.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ 360sdrun.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UmxCfg.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UmxFwHlp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UmxPol.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UpLive.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ upiea.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ AST.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ ArSwp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ USBCleaner.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rstrui.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KvReport.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQSC.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ghost.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KRepair.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SREngPS.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\XDelBox.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kpfw32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kavstart.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\knsdtray.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kpfwsvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kmailmon.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kissvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ appdllman.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ sos.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ UFO.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ TNT.Exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ niu.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ XP.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ Wsyscheck.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ TxoMoU.Exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ AoYun.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ auto.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ AutoRun.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ av.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ zxsweep.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ cross.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ Discovery.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ guangd.ex
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kernelwind32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ logogo.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ kwatch.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ QQDoctorRtp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ NAVSetup.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ pagefile.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ pagefile.pif
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ rfwProxy.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ SDGames.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ servet.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ KAVStart.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ mmqczj.ex
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ TrojDie.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RavMonD.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ Rav.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RavMon.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ RsTray.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ ScanFrm.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ rsnetsvr.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ arswp2.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ arswp3.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ zhudongfangyu.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ 799d.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ stormii.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ tmp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ jisu.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ filmst.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ qheart.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ qsetup.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ sxgame.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ wbapp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ pfserver.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ QQPCSmashFile.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ avp.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ avp.exe
病毒刪除注冊表:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\{4D36E969-E325-11CE-BFC1-08002BE10318}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\Directory\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers\SD360
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\RisingRavExt
HKEY_CLASSES_ROOT\Directory\shellex\ContextMenuHandlers\RisingRavExt
HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers\RisingRavExt
病毒修改注冊表:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
名稱:ShowSuperHidden
數據:0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
名稱: {871C5380-42A0-1069-A2EA-08002B30309D}
數據:0
病毒訪問網絡:
URL=http://www.vo***77.com |
